One of the first things I bring up when working with clients on cloud identity stuff, such as migrating to Exchange Online or rolling out a modern workplace concept, is security. Your identity is the key value in the security of your data, so you want to protect it as good as you can. MFA is not an option anymore, you should always deploy it. However, you might want to concider the possibility to enroll in MFA (i.e. setting up your autenticator app) to your corporate network. You can do so using conditional access!
Configuring the conditional access policy
To lock down the change of security information, like configuring MFA or changing your self-service password reset details, I create a new conditional access policy called Lock down MFA enrollment. I target it to ‘all users’ and set the ‘cloud app’ to ‘User action -> Register security information’.
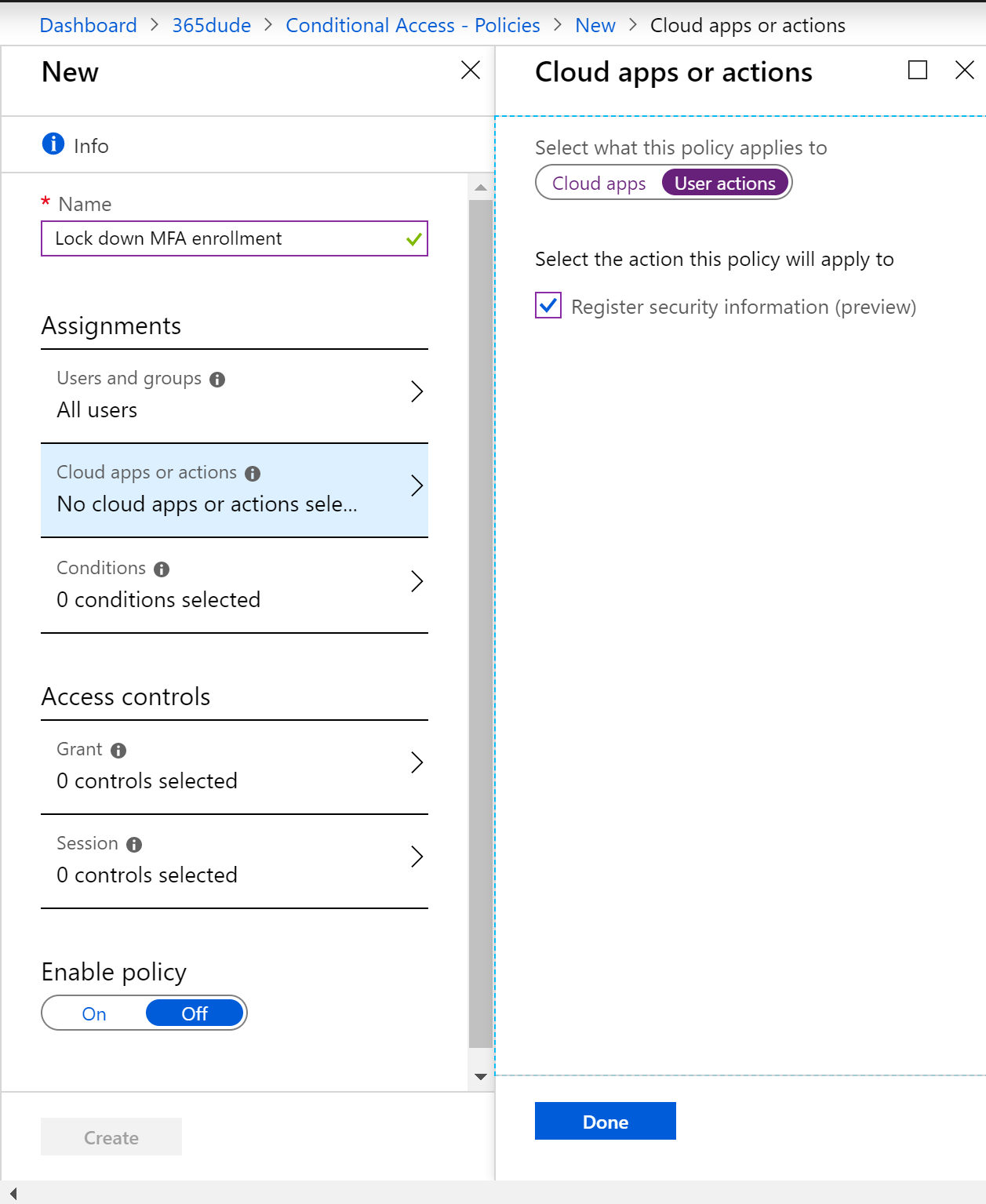
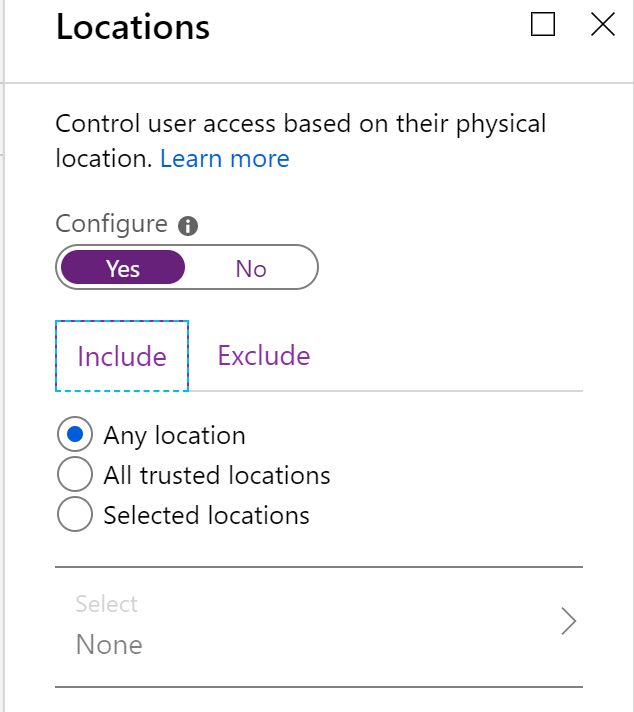
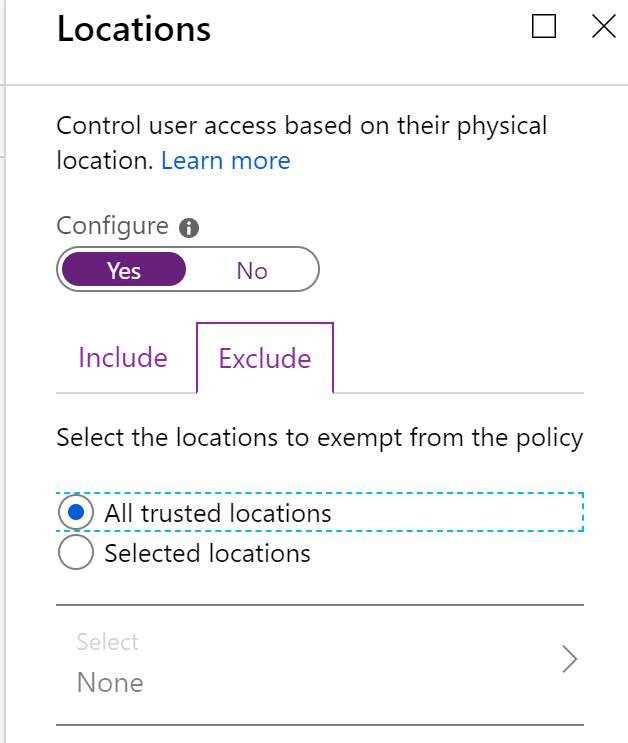
For the location, I set it to include any location, but exclude all trusted locations.
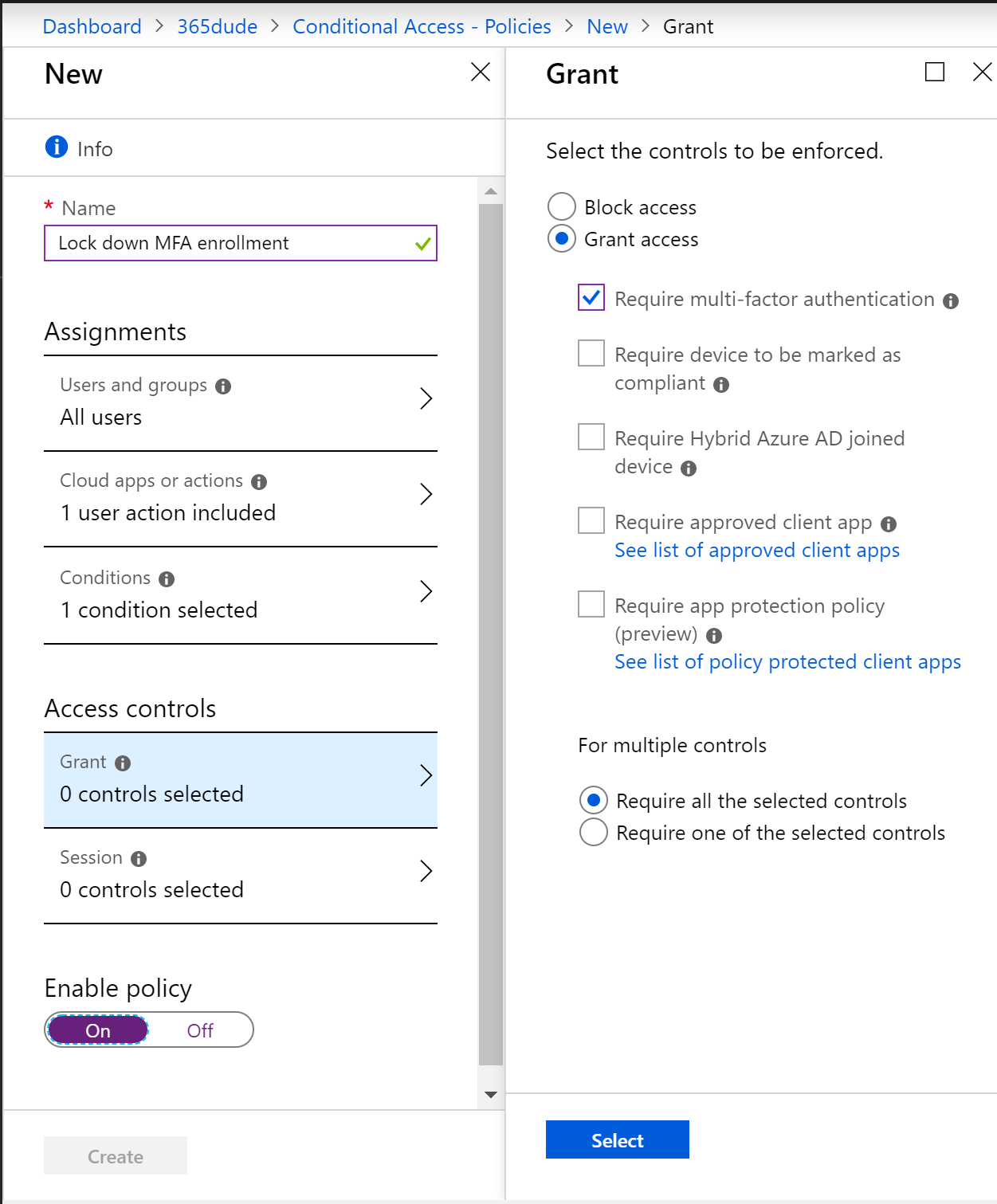
For the access controls, I set it to grant access but require multifactor authentication.
So, by enabling this policy, if a user tries to access the security information portal from inside the corporate network the policy isn’t applied and the user gains access. If this attempt comes from outside the corporate network, a user is prompted for MFA. If no MFA is already configured they won’t be prompted and are denied access because they can’t meet the required policy.
Prerequisite
This policy will only work when accessing the modern security portal, where information for both MFA and SSPR are combined. You can enable this new experience for (a group of) your users through Azure Active Directory. Go to ‘user settings -> Manage settings for access panel preview features’ and enable the preview features.
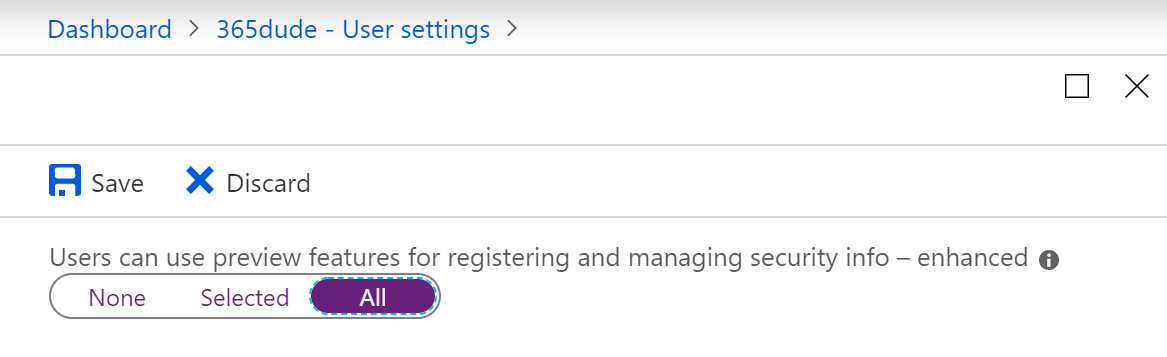
More on this new experience in an upcoming blog post :)
Setting trusted locations
In the policy I set the option to exclude trusted locations. But how do you define what the actual trusted locations are? You can set this from the condtional access blad, onder ’named locations’.
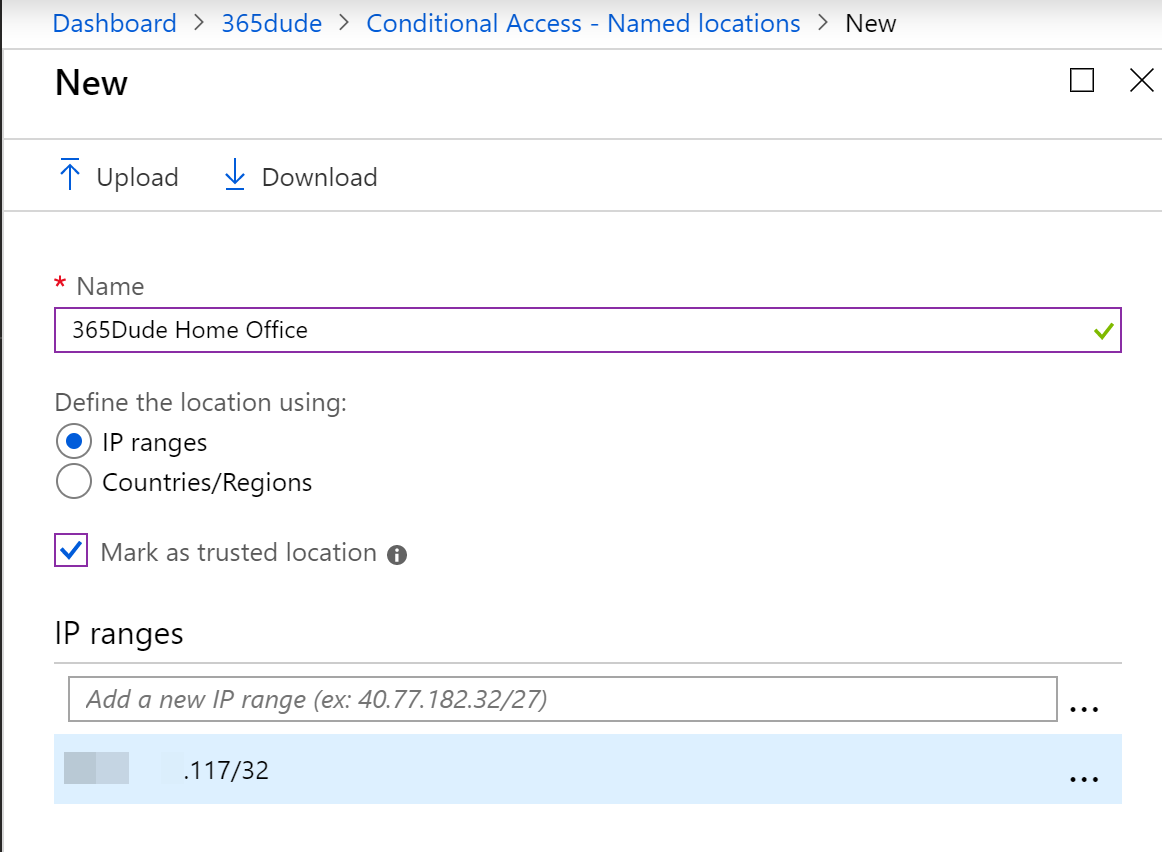
From here, you can add a location by specifying a CIDR-block and set the optional ‘mark as a trusted location’ checkbox.
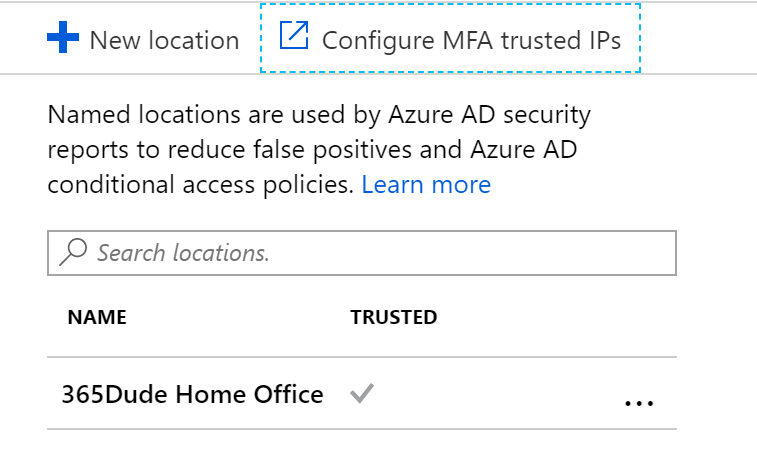
You can use this trusted locations in all your conditional access policies, for example to disallow certain functionality from outside your corporate network.