Using MFA to secure your modern workplace and productivity apps is a must, nowadays. However, you ofcourse do need something to create you second factor. Although the Microsoft Authenticator app does this just fine on any platform (and approving the push notification is a lot more convenient then typing over the code), there are people that don’t have a corporate phone and refuse their personal device for work purposes. Some of the recent MFA implementations I worked on were actually halted because of this.
Recently however, Microsoft anounced the public preview of OATH hardware tokens in Azure MFA. This solves this problem: clients get the possibility to distribute hardware OATH tokens for their users to keep on their keychain, which can provide them with the second factor in authentication. Just like the old days!
So, lets take this for a spin. For testing I used the Token 2 C101, but you can choose any supported token of your liking.
In my case, after receiving the tokens, I needed to fill out a form to let the supplier know the serial number of my devices, with the order number of my purchase. Token2 then sent me a CSV file with the secrets used for the tokens, that I can upload to the Azure portal. In this file, you need to specify the UPN of the user that will be using the specific token.
In the Azure portal, navigate to MFA and click OATH-tokens in the blade. Here, you can use the upload button to upload the CSV-file with 1 or more of the token details. When uploading is complete, you get a nice notification and after hitting refresh after a few seconds, the uploaded tokens appear in the pane.
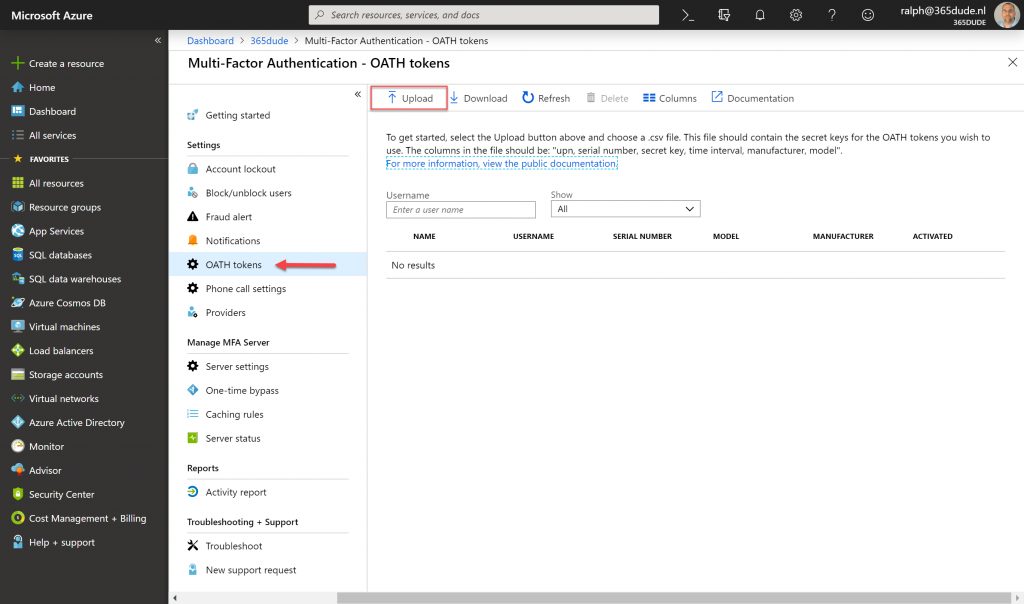
Here you can see the details of the token and the user it is assigned to. Before the token can be used, you need to click the ‘activate’ button to actually activate the token.
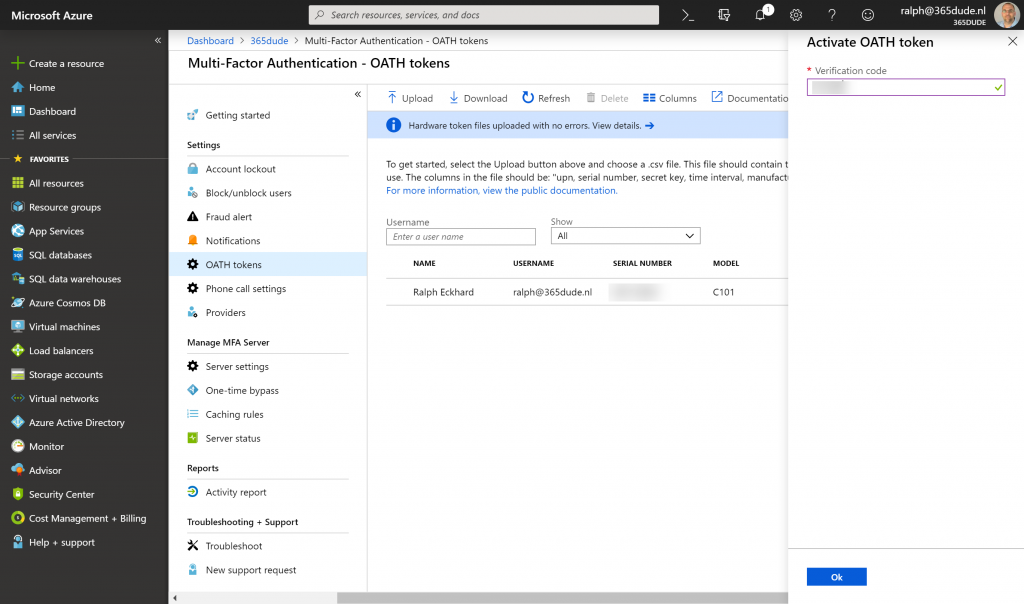
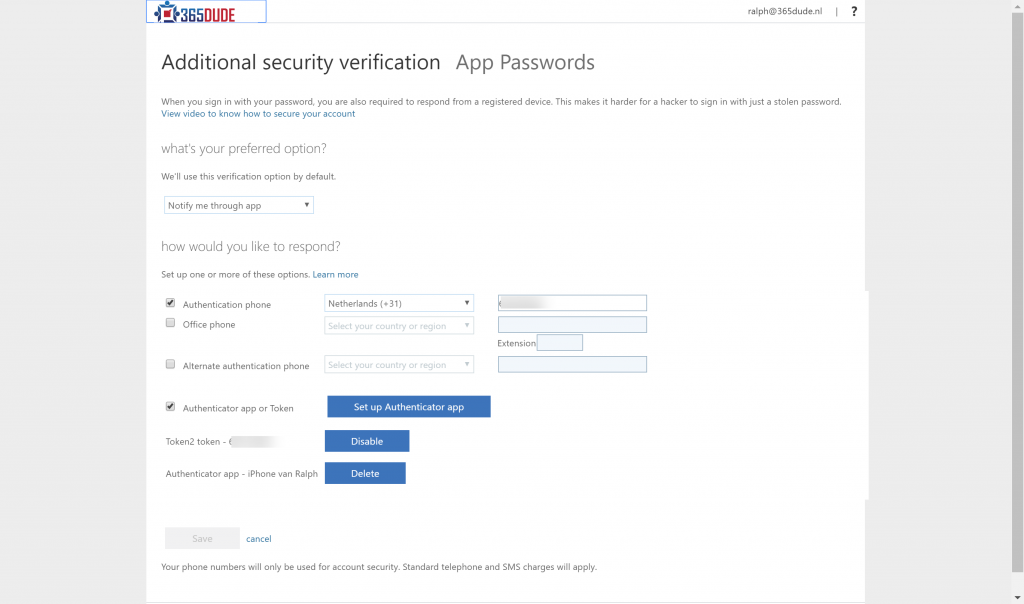
Here, you need to enter the code displayed on the token to validate the clock is correctly synced and the secret from the CSV-file is correct. After this, the token is linked to the MFA settings of the user and can be used to perform the second factor when authenticating. When checking the MFA settings for my user through https://aka.ms/mfasetup, I can see al the previous methods I had for MFA (like my phone number and the authenticator app on my iPhone), but also the newly added OATH token.
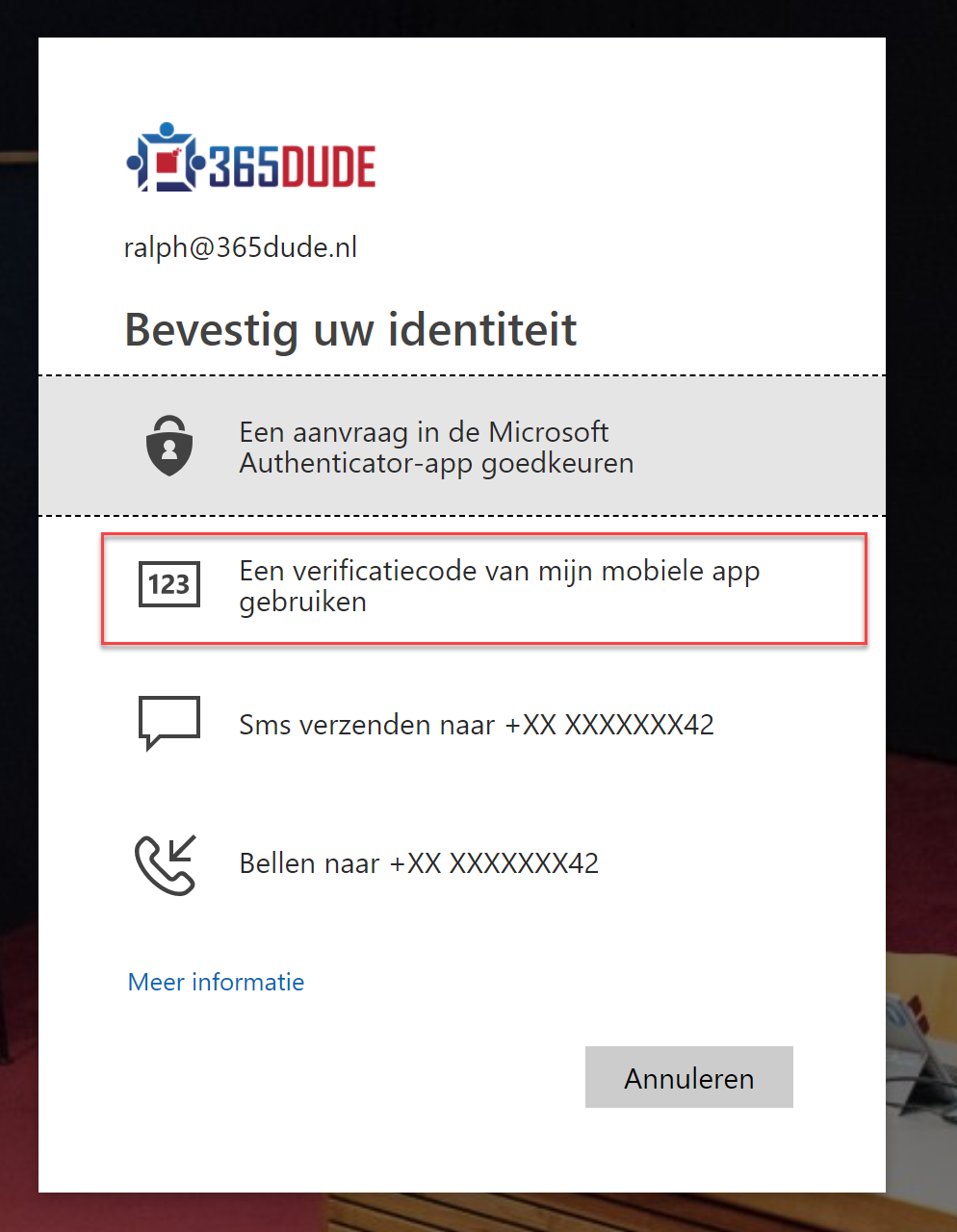
After this, I can use the token to perform MFA when logging in. When choosing the ‘mobile app verification code’ option I can enter the code displayed on the token and log in. Of course, you can set this option as your preferred MFA method through your settings.
So, pretty cool huh? Actually using a hardware token you can always have on you to perform MFA will unblock some of my clients to roll out MFA to personell not using a corporate phone, without the need to use their personal devices.
