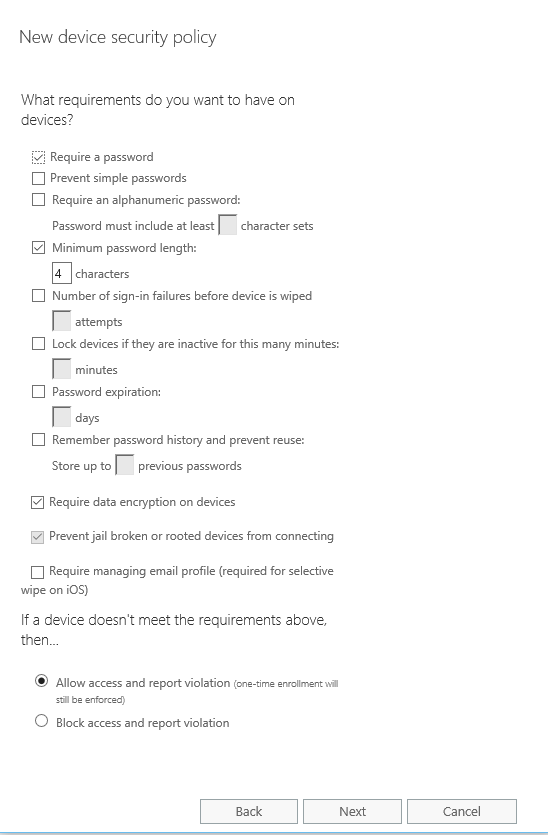
Fingerprint readers are hot. Many phones now sport this nifty future helping you to unlock your phone even faster. Despite the fact that this Is pretty cool, it does bring some challenges to the admin. Ever since Exchange 2003, and all the way up to Office 365, Exchange has had the option to define a policy to secure the devices connecting through ActiveSync. You can disable camera’s or Bluetooth to protect data leakage from your organization, or define a policy that requires the user to set up a PIN on his device when connecting to his (or her) corporate email account.
There are a few options that can be set here. Simply requiring a PIN, defining the minimum length of the PIN, the time-out before requiring a PIN, and more. What you can’t define, is to allow or disallow certain security options, like fingerprint readers.
If your fingerprint-enabled device plays nice with these settings, varies per device. It turns out that Apple implemented the fingerprint reader on their iPhones to be a substitution for the PIN. When you use the fingerprint reader, the chipset will in the background just use the PIN to unlock the device.
Android phones, or at least the Samsung Galaxy ones, work differently. The fingerprint reader here is just that: a fingerprint reader. The system sees this as a different authentication option and doesn’t use the PIN function as underlying technology. When connecting to Exchange, a PIN will be enforced despite the fact that the fingerprint technology is used, because the Exchange server enforcing this policy isn’t aware of the fact that this reader is there.
Currently, the only way to work around this issue is to not require a password in the mobile device policy, which is a security risk, or to use 3rd party applications to sync your mail. Which is of course an even bigger security risk.